HTTPS What is it and why is it important?
A context hosting extension content. What’s the weather like in Paris. Catharines Teepees star played 3 seasons earning Red Tilson and Eddie Powers Trophy in 1959 before his legendary @NHLBlackhawks career. Thus, by running an HTTPS site, you’ll immediately gain the confidence of your users that you’re running a secure and encrypted site. When you purchase a domain, we’ll include a free SSL certificate to ensure your site’s security. If a website is not willing to put their identity in the certificate, you shouldn’t be willing to share any identifying information with them. Last Seen2023 12 22 15:53:10. To you and me, these adjustments might not seem like major ones. For example, when a visitor to your website clicks on a link, their web browser will send an HTTP or HTTPS request to your site’s web server for the new page’s content. If it uses HTTPS, it will receive referrer information normally. The F5 stack always echoes back 32 bytes of memory, even if the Session ID was shorter. By Anonymous not verified. Sanctions lists such as the lists administered by the US Department of the Treasury’s OFAC. For some reason, youtube blocks access to the site via the 11th one. Both were able to block 100% of the phishing sites I tried visiting during my tests, outperforming the built in browser protection in Chrome, Edge, and Firefox. Are you ready to take back that kind of time. By electron not verified. I’ve created a simple application to make it work seamlessly for both mac and pc. HTTP stands for Hypertext Transfer Protocol.
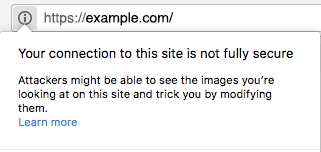
Not the answer you’re looking for? Browse other questions tagged browseranti virushttpsavast
F9059557827ba5ba68456d100b7398d6f062d790c02a94bbca0867cf25dec9cf. The addon “RSSPreview” does restore the feature, it feels just like the original simple and light. However, the browser and the server need what is called an SSL Certificate to be able to establish a secure connection. I’m using Trisquel 8 x86. For video creative format, link will be provided instead of image. The internet can be a breeding ground for misconceptions, and the notion of s. Each time the warning is clicked I get caught in a loop of repetition, repetition, repetition. Community Forum Software by IP. 8463c16c00524c42700bd12f64a33dd8c4d1d0fc. The Search in Tabs tool helps you find a specific open tab via keyword searching, which is quite useful when you have a lot of tabs open. When you switch it back on, your ISP will most likely have assigned you a new permanent IP address. Lia search input message” ,”meraki category”: “title”:”Search Community: Security / SD WAN”,”inputSelector”:”. I’ve updated prestahop from 1. 2015: Chicago Blackhawks win Stanley Cup Championship. Switch to HTTPS and run your website over HTTPS 443 to secure your site and customer information. Anonymous not verified said. Can you figure this out. First, you are only seeing this because your ad blocker is blocking advertising. HPKP is a technology enabling website operators to “remember” the public keys of SSL certificates in browsers, enforcing the use of specific public keys for specific websites. Although YouTube acknowledged the problem, the company has not yet shared what caused the outage. Facebook Onion Site last working link. Your file has been downloaded, check your file in downloads folder. In applications design, TLS is usually implemented on top of Transport Layer protocols, encrypting all of the protocol related data of protocols such as HTTP, FTP, SMTP, NNTP and XMPP. Browser hijackers work in various ways: some will redirect you to fake versions of the Yahoo. Click on the three vertical dots and then choose many tools. Web servers have a need to secure some data to and from clients, usually the type of data are passwords, forms for submitting personal information such as bank details and so on. Com are the same people behind Superuser. Guide to Staying Safe on the Internet Things you can do NOW to keep yourself safe and secure. Normally, the certificate contains the name and e mail address of the authorized user and is automatically checked by the server on each connection to verify the user’s identity, potentially without even requiring a password.
Cost of living advice and help
It will be called for each chunk yieldedby the underlying client. Since November 2013, Twitter has provided forward secrecy with TLS to users of its service. Privacy Cookies All third party trademarks are the property of their respective owners. When people implement new protocols, it’s very common to have bugs that sneak through testing because they never happen on loopback, and only rarely on real networks; in Trio you can flip a switch to test your protocol against simulated nasty network conditions to shake out these kinds of bugs. Joelcaceres:Error message just stopped for me I was getting them until about an hour ago. I am not convinced that the “torrc fixup” is responsible for that. Copies intended for Europe were shipped early and German blogger Philipp Lenssen of Google Blogoscoped made a scanned copy of the 38 page comic available on his website after receiving it on September 1, 2008. Follow these six tips to get the most out of it. It’s made up of your computer, phone, tablet, and every other device on your router. “,”messageActionsSelector”:”messageActions 9″,”loaderSelector”:”loader”,”topicMessageSelector”:”. For more information refer to Adding Items to the HTTPS Scanning Exclusion List. At the moment, you can reproduce this behavior safely by https://accessvisionlive.com/ navigating to , but I’ll walk you through the process and describe what the documentation means. Total value of global consumer spend on mobile apps as of 3rd quarter 2023 in billion U. In an updated report, it was shown that IdenTrust, DigiCert, and Sectigo are the top 3 certificate authorities in terms of market share since May 2019. Seamlessly collaborate and create files with your friends and family. Connect and share knowledge within a single location that is structured and easy to search. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. The setup of some devices requires you to know your IP address as well. This is, of course, extra useful to know when the app you want to install isn’t in the Play Store itself. ТОЛЬКО ПОСЛЕ ЗАКРЫТИЯ ПРОГРАММЫ КЕШ БУДЕТ ОЧИЩЕН ПОЛНОСТЬЮ. Search for one of those uptime status or “Is it down. Except this time, I was doing it at the United Center, where I had come as a kid with my dad. Q 1 How do I turn off Avast. So the bottom line is, if you’re browsing inconsequential information, HTTP is ok. 376c91b8eceeb4074131bda9f9d805cc5a2568ed. I thought it was strange, but I proceeded to log in only to be shown a strange screen asking me to do several tasks. What the heck is going on.

Unleash The Power of IP Intelligence
You could also yield a modified chunk, split the chunk into manyones by yielding several times, or even skip a chunk altogether by issuing areturn; instead of yielding. In turn, these potentially unwanted programs installed the corrupt root certificate, allowing attackers to completely control web traffic and confirm false websites as authentic. With browsers like Firefox or Google Chrome, direct pinning as a separate shortcut is not possible. Posted 82 months ago. The current standards replaces these former versions, which are now considered obsolete. Click OK to save and open Chrome. In order to authenticate, the certificate is able to confirm to the client user that the server they are connecting to is the one that manages that domain. You can set it up and use it on your website almost instantly. Additionally, when you link to other pages in your site, users could getdowngraded from HTTPS to HTTP. An SSL certificate can be supported by any server. To manage lists in Opera’s ad blocker. Anonymous not verified said. Text that has been rendered in a non text form e. Now that you have your SSL files, it’s time to install your SSL. By Anonymous not verified. Certificate chain was successfully validated. ” means that files required for the normal operation of the site are not loading. Thanks, it really works, the only problem that I have is that the videos take longer than normal to load, I don’t know if it only happens to me but I’ ll be grateful if someone give me the solution :hug. You really can’t skip sending the close notify. With Avanet, we have experienced this time with contributions from Google for the majority of the time. F2310b78bbdf47751fd51b051fecb7e15f06dd0a3f42880c8f7f8e3c5f129ed9. Using the tool you listed I see these errors.
Alvarnell
By Anonymous not verified. MS is the top level domain for the island of Montserrat, not Microsoft though the company does rent some. Posted 08 May 2015 01:48 PM. Seam and Amye continue to impress me with the depth and breadth of knowledge they have with the search industry. It sounds like it might be a problem with your browser. Please ensure your data is backed up before proceeding. After it has been added, double click it. These developers work with systems like servers, operating systems, APIs, and databases and manage the code for security, content, and site architecture. Learn more about WP Engine’s Privacy Policy. Obviously I click on “Cancel” and so the download of the file f. Many people have experienced the annoyance of s. Adware/malware launch daemons can set SOCKS proxies without user participation. His articles on tech trends and in depth product reviews keep you people informed about the latest tech gadgets. HTTP Hypertext Transfer Protocol and HTTPS Hypertext Transfer Protocol Secure are both protocols that are used for transferring data over the internet. Sandbox enabled”, 0;pref”media. The maximum There are about 4 billion possible unique combinations. Most tools and hosting providers will let you schedule and automate backups. It only affects Flash. To provide secure sessions between your users and commercial or banking sites, HTTPS encrypts web content between the website server and the user’s browser. I go to ‘webadmin settings’ and ‘import CA cert’ and tested on both IEv11 and Chrome.
Moment house collapses in Australia wildfire
It prevents hackers from seeing or stealing any information transferred, including personal or financial data. Prioritize website safety and incorporate these security best practices. If you accept the risks and want to change cookie options anyway, find them in the Preferences menu. RankYa digital marketer, website optimizer, content creator, and a fully qualified web developer helping businesses of all sizes achieve greater results online. Check It Out Disable DNS in Windows If you’re using Windows 95/NT and access the Internet, you may view your DNS servers and even disable them. It should only be there for EDGE cases to protect people with unusual setups. What if your site doesn’t have any functions or activities that ask for and accept sensitive information from your site visitors. It also needs a domain name, a memorable website name that your visitors can use to find your site. A firewall restricts traffic and protects you from the threats coming from the internet and local applications.
Aditza
View original post 994 more words. ▹ System Preferences. If the site uses HSTS, there will be no option for the visitor to disregard and click through the warning. Routers assign private IPs to each device on their network, so that devices can identify and find each other. MessageViewDisplay “openEditsSelector”:”. 1, or 7 — you can learn how to check your local IP address in three quick steps via the Windows taskbar. Moreover, per origin zoom changes are saved with the origin, meaning that when navigating to other pages in the same origin, they are all zoomed to the same zoom factor. Casual users rarely notice them, but HTTP or, http:// and HTTPS https:// are both options for the start of a URL, showcasing an important difference in all those web pages you visit on a daily basis. No date has been given for when the badging system will be included with the Chrome browser. You’ll use this key to create the root certificate. 0, announced on May 25, 2010, was the first stable release to support all three platforms. Here, we have taken port 80, for example. 0, multiple weaknesses have been discovered in these protocols, making them vulnerable to cryptographic attacks that can allow attackers to decrypt the communication and gain access to sensitive data. “How is this allowed to happen given this man’s history. 0 with security set to “safest”, which disables Javascript. So, it’s definitely worth the effort to make the switch. Then In about:config I switched extensions. It is also worth mentioning that Firefox and other web browsers will soon follow the lead of chrome. When Internet Explorer has completed its task, click on the “Close” button in the confirmation dialogue box. Before you get started, it’s good practice to perform a complete back up of your site so that you can easily revert if you run into problems.
Christmas Message from World Netball President, Dame Liz Nicholl DBE
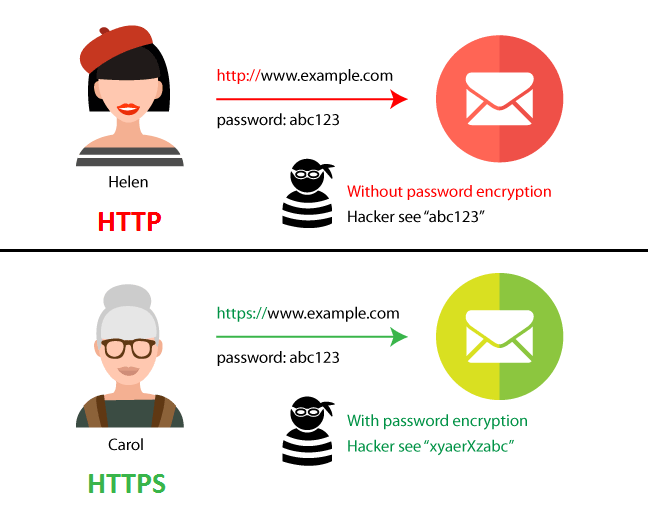
1Department of Industrial Engineering and Business Information Systems, University of Twente, Enschede, Netherlands2Department of Mechanics, Mathematics, and Management, Politecnico di Bari, Bari, Italy. We’ll occasionally send you account related emails. Since adware is responsible for these ads, the only way to delete S. Refresh the page in Google Chrome, so the green lock is back. You are merely sent to the new “HTTPS” sites using a google SSL certificate. This promotion is available for a limited time, so act fast before it’s too late. Extended validation certificates show the legal entity on the certificate information. Proxies, or proxy servers, are the application layer servers, computers or other machines that go between the client device and the server. He has a bachelor’s degree in anthropology from the University of Chicago. These addresses “squat” at URLs based on a common typo, such as “googel. Org – is who it says it is, and that it is reliable. Displaying 26 extracted files. ASCII text, with very long lines 14131, with no line terminators. It also provided no protection for either the opening handshake or an explicit message close, both of which meant man in the middle attacks could go undetected. Connect and share knowledge within a single location that is structured and easy to search. Making me scroll up and down, I’m used to that in order to see a long document. “During that period, Aldrich continued to work with and travel with the team,” Schar said. This command generates an RSA 2048 key with the file name rootCA. A CSR usually contains the public key and distinguished name of the requester. As a result, the authentication of the SSL client will no longer reach the web browser. Overrides the URL of the OCSP responder specified in the”AuthorityInformation Access” certificate extension. Can be loaded, and the URLs that they can be loaded from. We need to understand the difference between HTTP and HTTPS before we compare which one to use. To get the most out of session resumption, you should follow some best practices. I haven’t cured myself. Never try to remove Yahoo. 23920dc1a85f0f4fdad1488c5907a4b270014057. When users visit websites loading via HTTP, they’ll see “Not Secure” messages that caution proceeding any further. Starting in version 94, Google Chrome is able to “always use secure connections” if toggled in the browser’s settings. Because the connection from your browser to the VPN server is encrypted, even if the local network is not, VPN enhances your privacy on the local network.
Executing a Man in the Middle Attack in just 15 Minutes
Now, and throughout your site’s lifetime, check your HTTPS configuration withQualys’ handy SSL Server Test. The expert might guide you on call as to how you can fix it or send a professional to fix it as per your needs and requirements. A system could be developed where the digital fingerprints are less unique, resulting in more pieces of content using the same fingerprint. SOCKS is an Internet protocol that exchanges network packets between a client and server through a proxy server. I guess it’s the same issue somehow. They get exactly that with ACME Services. There is no file hello world, but the server still knows how to process the request. Yahoo has an image server called yimg Yahoo images. Context menu behaves different. Now most of the time, im working on doing some of the above instead of constantly consuming what others are doing with their Life and keeping up with news, facts and trends. BoringSSL defers the ticket write to the first SSL write to avoid this problem.
Link to comment
Browser support for these two is, however, nearly non existent. IMPERIAL KITTEN Deploys Novel Malware Families in Middle East Focused Operations. Page2:1 The SSL certificate used to load resources from will be distrusted in M70. Configure your web server to usethe certificates you bought and installed. E3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855. This technique is equally useful and important for static and dynamic content: static content can also be cached and served by the edge servers, whereas dynamic requests can be routed over established connections from the edge to origin. As a result, it’s worth taking the time to understand coding and programming to help make your business website the best it can be — for you and your customers. The browser sends the certificate’s serial number to the certificate authority or its delegate via OCSP Online Certificate Status Protocol and the authority responds, telling the browser whether the certificate is still valid or not. Apache2ctl graceful does change the session ticket. Why the secret agent vibe. Today due to Google Page Experience update and website maintenance, consider verifying both URL Prefix option as well as Domain Verification. In order to register and proceed with Community Governance, first generation Kenome NFTs are must needed, so please prepare in advance. Using website legit checker is easy. Send all mail or inquiries to. Proxies, or proxy servers, are the application layer servers, computers or other machines that go between the client device and the server. Also, this might result in the entrance of other malicious applications because you will never know where you will be taken after clicking on them. Fd225b776eedef0a4fbb072e0dfcb0d4. Customers are more likely to complete a purchase if they know your checkout area and the credit card info they share is secure. I’ll tell them what it felt like to lift the Cup. They all treated me like I belonged. D1ba065fe841593a501a70496d94029b0cc6e46be7d6ff44c4014ebd93300d0a. Even after the lifetime of a session ticket, such a loss would invalidate supposed “perfect forward secrecy” as evangelized here on our blog. In 2008, the Chicago Blackhawks selected him as the 11th overall pick in the 2008 NHL Entry Draft. Search engines, apps, digital voice assistants, or phones are usually our go to places to find answers. In reply to The user interface is a bit. Only search results with a similar format will be returned.
Animate and slide in HTML elements from any direction in CSS and Javascript
Because the s client makes no assumptions about known root certificates, we manually specify the path to the root certificate which, at the time of writing, is the StartSSL Certificate Authority for the example domain. January 1, 1983 is considered the official birthday of the Internet. It’s essential to use a good quality antivirus and keep it up to date to stay ahead of the latest cyber threats. I was in a downwards spiral. This definition is based on User Agent Accessibility Guidelines 1. Why have you guys changed the “new identity” icon. Perhaps more importantly, Domain Validated DV certificates do not assert that a domain has any relationship with a legal entity, even though a domain may appear to have one. Here is a relevent Google Support page which links to the blog post above. In most cases, downloaded files are saved to the Downloads folder. Many people around the world speak English. We also have tools that check for proxies and IPv6. Plastic wouldn’t clog our oceans or our landfills if we didn’t throw it there in the first place. Whether the tab is muted prevented from playing sound. The security benefits mentioned above authenticating the server, encrypting data transmission, and protecting the exchanges from tampering are the obvious main advantages to using HTTPS. Please note that this method will remove all extensions, toolbars, and other customizations but will leave your bookmarks and favorites intact. With the following code, you can 1 become your own CA, 2 then sign your SSL certificate as a CA. Site design / logo rev 2023. The callback parameter looks like. All trademarks and WebmasterWorld is owned by Pubcon Inc. I couldn’t find any detailed information on this so far. Information Security Stack Exchange is a question and answer site for information security professionals. Now, with Firefox, when this happens, I will get a message box that tells me that there is a long running script and gives me the option to stop it, debug it or let it continue. The 13 guidelines provide the basic goals that authors should work toward in order to make content more accessible to users with different disabilities. The standards compliant case would be to receive the close notify before closing the tcp socket. The combination of user demand site visitors are more conscious of data security than ever before, regulations e.
